How to give Orchestrator API access to your Azure account
You may need to get API access to your Azure subscription, either because you want to have a "BYOS" subscription of the Multi-Cloud Orchestrator, or you want to deploy an Instant Cloud Solution from the marketplace.
This operation is structured in 3 parts:
- Select the Azure subscription to be used
- Register an App in the Azure Active Directory and retrieve subscription credentials
- Assign the new App in the Azure Active Directory the "contributor" role
Note: All 3 parts of the procedure must be successfully completed for the API access to be valid.
Credentials to be extracted
- Tenant ID
- Client ID
- Client Password
- Azure Subscription ID
Roles to be assigned
- “Contributor” role to Azure Active Directory App
Select the Azure subscription to be used
- First, go to http://portal.azure.com navigate and login into to the Azure portal. Select All services from the main menu.
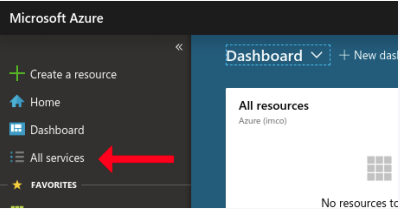
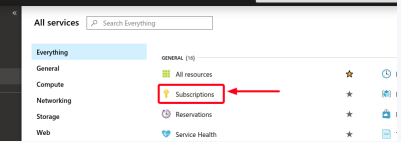
- A new window will pop-up with a list of services. Click on the Subscriptions section.
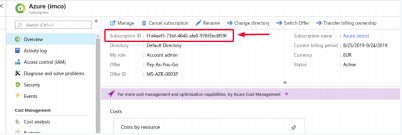
- Select the subscription. It will pop-up a new screen showing the required information.
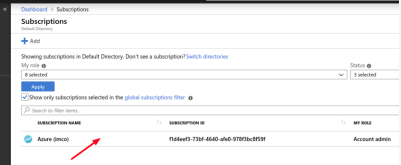
- Highlight the Subscription ID and copy it.
Register an App in the Azure Active Directory and retrieve subscription credentials
Note: In order to get the Client ID and Secret, we need to create an Azure Active Directory application and service principal that can access resources.
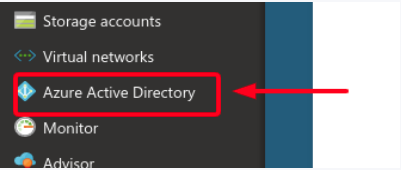
- Click Azure Active Directory from the main menu.
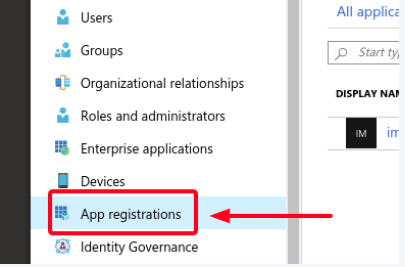
- Click on the App registrations section.
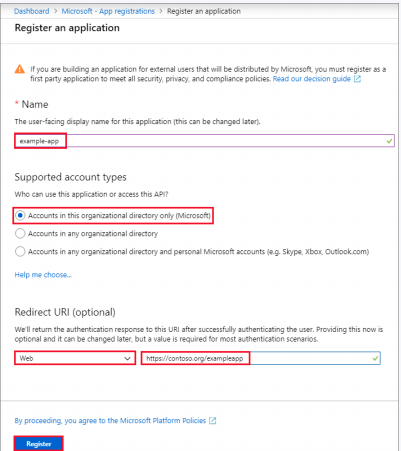
- Name the application, select a supported account type and a redirect URL if needed, and register the application.
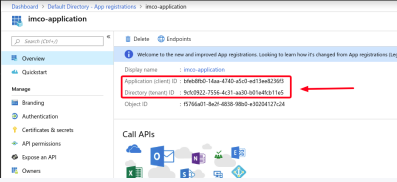
Assign the new App in the Azure Active Directory the "contributor" role
- Select the Certificates & secret section.
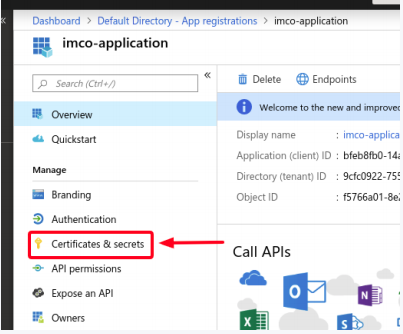
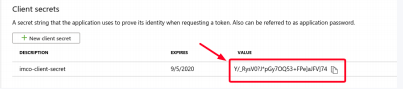
- Add a new client secret.
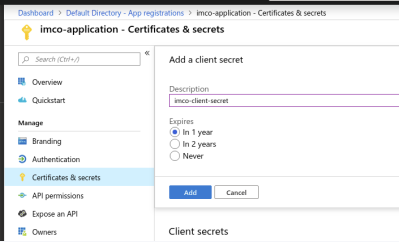
- Add the client secret you had created in the previous step and copy the value. *you must assign the application to a role
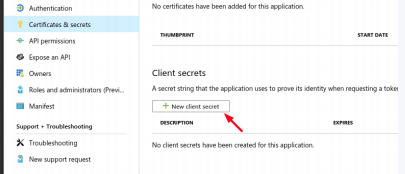
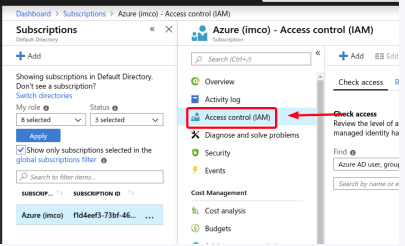
- Go back to the Subscriptions section (All services / Subscriptions), select the subscription and click on the Access control (IAM) section.
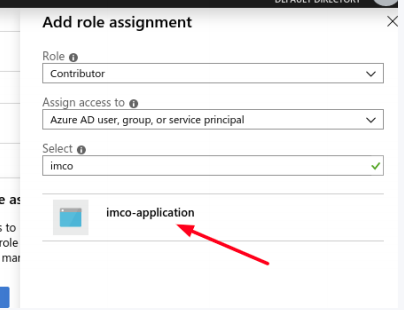
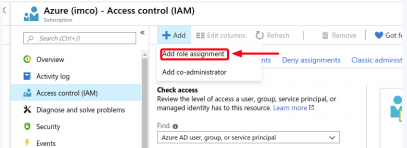
- Click on Add role assignment.
- Select the role you wish to assign to the application.(to allow the application to execute actions like reboot, start and stop instances, select the Contributor role).
- Then, start typing the application name in the Select input. Select the application from the results and save the assignment.